SushiSwap is a decentralized exchange (DEX) that uses Automated Market Makers (AMM) and operates on the Ethereum blockchain. It was founded in 2020 by an unidentified person going by the pseudonym "Chef Nomi." However, Chef Nomi left the project in its early stages of development, and was replaced by "0xMaki", one of SushiSwap's first employees.
The current CEO of the company is Jared Grey.
In addition to DEX functions, SushiSwap provides users with a cryptocurrency wallet, liquidity provider options, cryptocurrency exchange and lending services. It also has its own native SUSHI token, which users receive as a reward for providing liquidity.
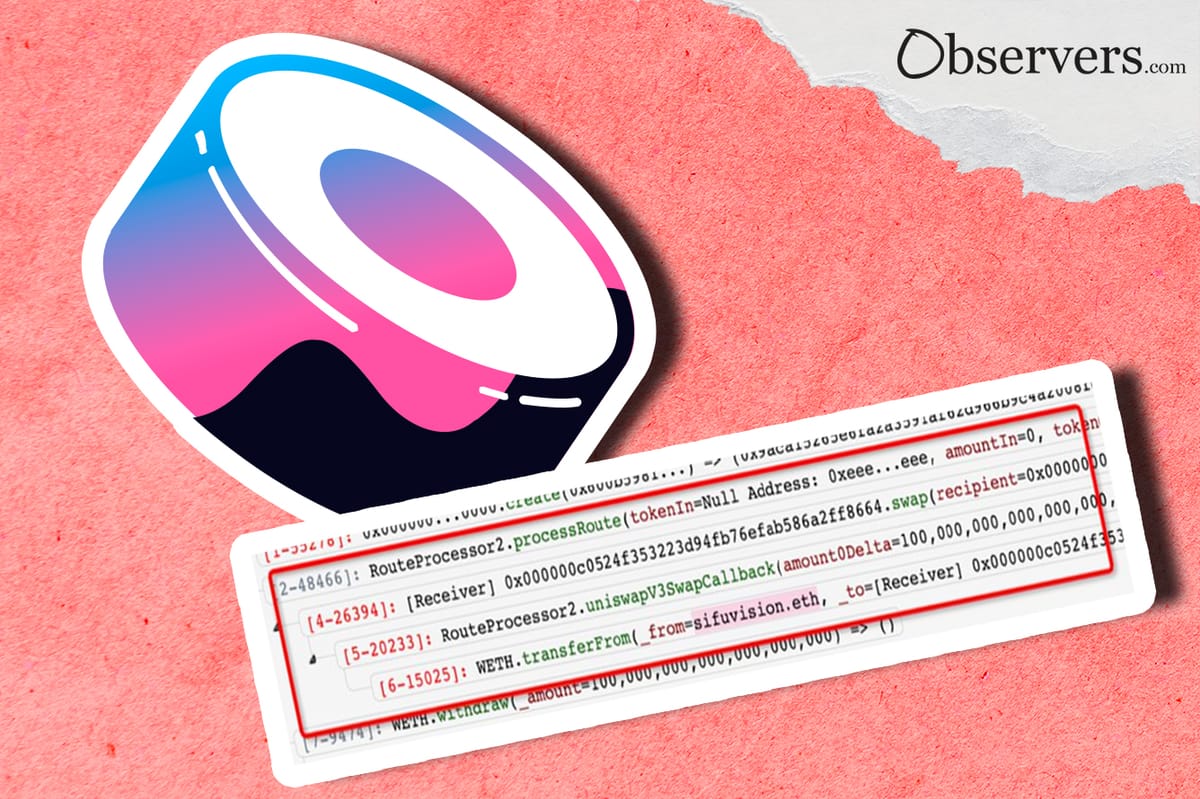
In the first half of April, SushiSwap experienced an attack on its "RouteProcessor2" smart contract, used to determine the most profitable price during token swaps.
PeckShield Inc., a company involved in data analysis and blockchain security, announced the attack. According to the company, the exploit cost user @0xSifu approximately 1800 ETH (or more than $3 million).
CEO of SushiSwap Jared Grey was quick to confirm the vulnerability. Additionally, he urged anyone using the RouteProcessor2 contract to "revoke approval ASAP."
Sushi's RouteProcessor2 contract has an approval bug; please revoke approval ASAP. We're working with security teams to mitigate the issue. https://t.co/WhXJfa5xD4
— Jared Grey (@jaredgrey) April 9, 2023
The vulnerability was exploited by an unknown hacker. As explained by 1Inch’s Anton Bukov on Twitter, the hacker used a fake UniswapV3 pool with the new SushiSwap router, which did not verify the authenticity of the pool.
The company BlockSec, which conducts smart contract audits, was able to recover 100 ETH that belonged to @0xSifu. Unfortunately, it was impossible to recover the remaining funds, BlockSec stated on Twitter.
SushiSwap published a brief report about the attack on April 12th. In it, they claimed that the web version of Sushi's Swap was currently safe to use.
The exchange also asked its users to check any remaining approvals for tokens connected to the RouteProcessor2 contract, adding that those who had not used SushiSwap before April 2 were safe, as the vulnerable contract was created after this date.
On April 18, SushiSwap published a report on the exploit that included information on how the funds were stolen, how much they were able to recover, and how developers were planning to address its consequences. Strangely enough, a new theft of 94.9 ETH occurred while the report was being written.
The fact that the smart contract was "non-upgradable, non-pausable, and users' access couldn't be revoked preemptively," according to the team, made it difficult to address the vulnerability.
The company also outlined the process for returning users' lost funds. "Funds swept by whitehat security teams" were promised to be returned right away, and "funds lost to blackhat hackers" were promised to be reimbursed from their treasury following an investigation.
Take care of your funds, dear readers. And we continue to Observe.

